With hacking techniques and cybersecurity threats evolving all the time, particularly with the fast growth of AI in recent months, email security has become a critical aspect of safety at work and at home.
Hackers can use your email both for the content and as a way into your organization to conduct a breach of the larger network. Once in, hackers can slither their way into many files, from confidential financial records to personal information. Here you will find helpful information about the common threats to email security and ten best practices for a robust email security solution.
Threats to email security
The following are some of the most common threats to email security.
- Phishing
Phishing is an attack that asks you for money or valuable information such as account logins or passwords. Spear phishing is an attack that uses your personal information to get valuable data by impersonating someone you know.
- Spoofing
Spoofing is an attack where false data is provided to seem legitimate, such as sending an email from an account that appears to be an official banking email address.
- Malware
Malware is a computer virus, a type of software that can get downloaded to your device, which is designed to disrupt a device, server, or network and generally causes havoc. Malware is a significant threat to email security and can be easily downloaded through spam when hackers use it to insert malicious links, malware, and trojans. Therefore, it's crucial to take appropriate measures to protect your email accounts and the contents of your emails from cyber attacks and online security threats.
Malware can also embed itself in startup items to auto-activate on system boot, making detection and removal tough. This highlights the need for regular system scans and monitoring of startup programs to safeguard against these security threats.
- DoS attacks
A DoS attack, or denial-of-service attack, is when a hacker makes a machine or network resource unavailable to users by disrupting the services of a host connected to a network.
- Increasing and evolving cyber attacks
Cyber attacks are becoming increasingly sophisticated as AI evolves and helps hackers to write more convincing emails. This is why it’s essential to develop a robust email security solution.
12 best practices for a strong email security solution
So, with all of the above in mind, let’s delve into some ways to mitigate the risks posed by cybersecurity with some simple best practices that you can apply immediately.
1. Make strong passwords and encryptions
We all know that we should use strong passwords and avoid using the same one twice, but it can be a real pain. Sometimes remembering your phone number is challenging, let alone dozens of passwords. Luckily, many devices can safely store your passwords so that you don’t have to enter them each time, and some apps store your passwords for you.
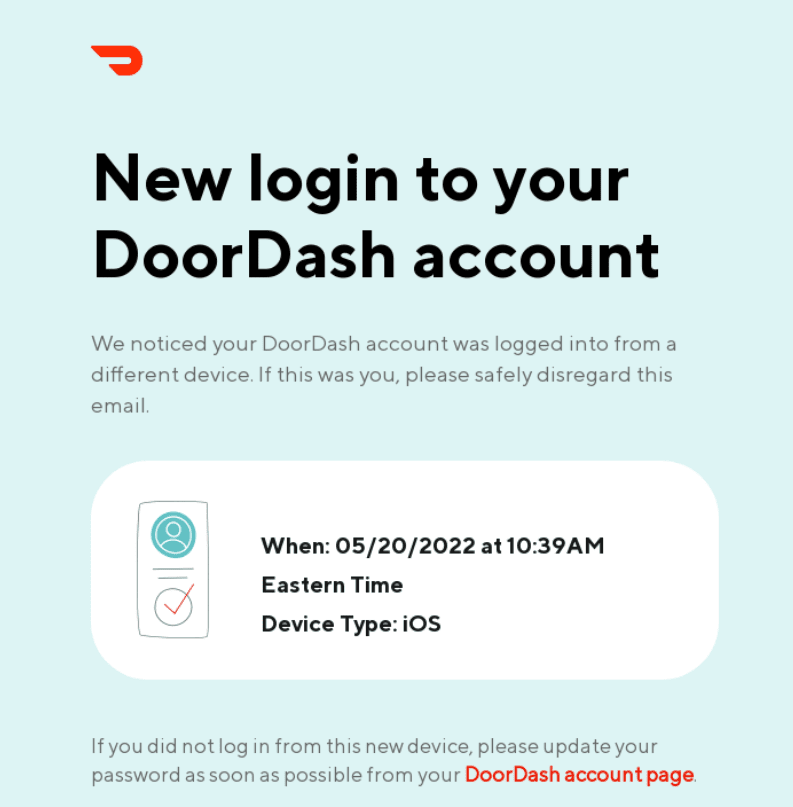
(Source: Really Good Emails)
Next, we have encryption: every time you send a thank-you email (or any email for that matter), there is some risk that it will be intercepted by a hacker on its journey between you — the sender — and the recipient. So what does encryption do? It scrambles your email’s content so anyone intercepting it can’t read it. Only with authentication from the recipient can the real message be read. This also means that if you accidentally send an email to the wrong address, the recipient won’t be able to read it.
Many email services, such as Gmail and Microsoft Outlook, as well as secure email providers like Mailfence, offer encryption as a feature. Protecting your internal audit report example and other essential documents becomes much easier with encryption.
2. Back up your important emails
As well as protecting your data from being seen by unwanted eyes, you also want to protect it from getting lost or deleted. This is why it’s a great idea always to back up any important emails. You can opt for an external hard drive or a USB stick or upload data to the cloud.
There are benefits and drawbacks to all of these. A physical external hard drive or USB stick can get lost or damaged, so you’ll need to consider securing your devices behind physical security systems to mitigate these risks, and there have been instances in the past of hackers getting into cloud storage solutions and stealing data that way.
There is no perfect solution, but security for cloud storage has improved over time. Having a physical copy of your important data can help if your device decides to exit the land of the living.
3. Educate everyone about suspicious emails and links
While a lot of cybersecurity comes down to tech, a good amount of it is about common sense and teaching best practices, such as how to recognize and deal with suspicious-looking emails or use email tracking software. You can run simple webinars, use video tutorials to simplify the process and add a quiz to ensure everyone has reached a specific standard across the organization.
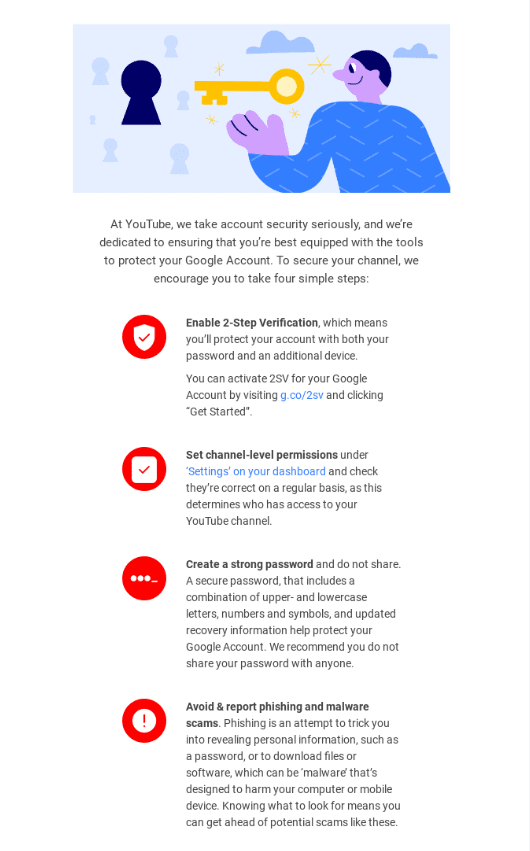
(Source: Email from YouTube)
Annual refreshers with updated information would also help the process, and you can check out the SOC 2 certification cost if you want to go the extra mile with training your staff in all things audit-related.
4. Keep your accessibility confidential
Proxies and USA VPN servers allow you to keep your location information private, send emails and conduct online research without worrying about Google third-party cookies tracking you. Specifically for emails, proxies allow you to send them without exposing your IP address.
So how does it work? Proxy servers act as a gateway between you and the internet, separating you and other users from the websites you browse. Internet traffic goes through the proxy server to the address you typed in. The request comes back through that same proxy server, and you are forwarded the data received from the website.
5. Install up-to-date antivirus security
You can’t just ignore your antivirus and leave it in the corner. It needs attention sometimes, so don’t ignore those pop-ups telling you that you need to download the latest version of the app. An old version will quickly become obsolete against the constant tide of hacking, so ensure your defenses are fortified with the latest updates and reliable email security tools.

(Source: Really Good Emails)
6. Improve your spam filter
You can use an email content filter to intercept incoming messages and check them for malware or other dangerous elements. After this process, your “How secure is RDP?” email gets delivered to its destination or quarantined for you to review if necessary.
Screening incoming communications before they reach you or your organization can protect you massively. This process allows you to look at messages without opening them and block spam messages and malware before they can reach your colleagues’ inboxes.
Another effective way to improve email security is to use email verification tools. These tools can help ensure that only legitimate emails are delivered to your inbox while blocking spam and phishing attempts.
With so many options on the market, knowing which tools are the best for your needs can be difficult. To make the selection process easier, it's worth checking out some of the best email verification tools available and finding one that suits your organization's requirements.
7. Make your email marketing contact list secure
This is crucial for maintaining your customers and audiences’ trust. After all, digital security is not only about your data but also your customers' data. When it comes to email, this means taking care of your email marketing contact list.
To do this, you should make sure you limit who has access to your email marketing list and store it securely in limited places (e.g., in a secure database). This is because the more people that have access and the more copies that exist, the more likely it is that the list will be compromised.
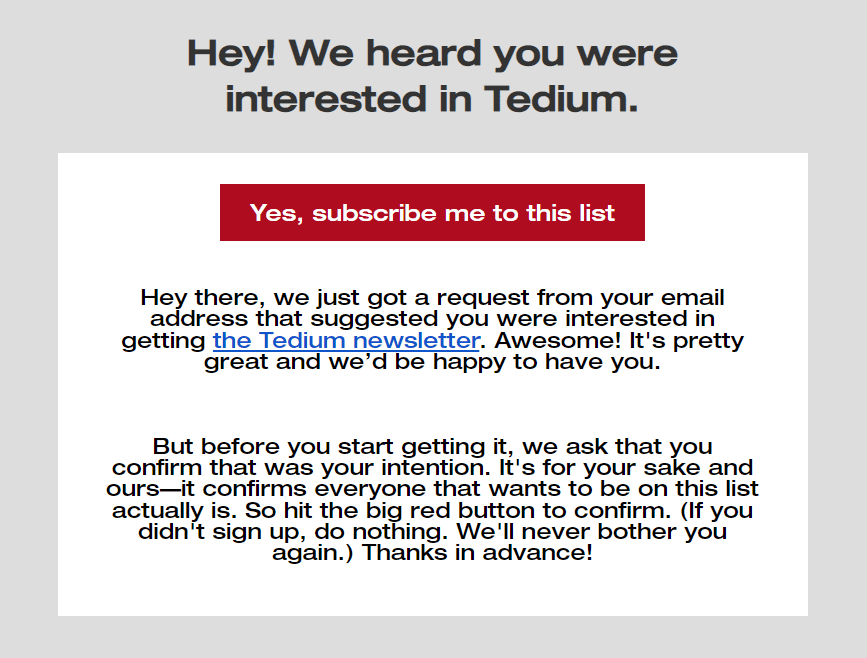
(Source: Email from Tedium)
You could also consider setting up a double opt-in sign-up process, which creates an additional step for customers to subscribe to a mailing list. This will reduce the likelihood that your marketing emails are being sent to bots or invalid email addresses, as well as assure your customers that they won’t be receiving emails they don’t want.
8. Enable SPF, DKIM, and DMARC authentication
There are three types of email authentication that you can configure: Sender Policy Framework (SPF), Domainkeys Identified Mail (DKIM), and Domain-based Message Authentication, Reporting & Conformance (DMARC). Together they help mailbox providers and spam filters to recognize that your email is legitimate and can be trusted.
This fulfills two objectives. Firstly, they are essential configurations that protect your brand’s reputation. This is because they reduce the likelihood of an unauthorized user sending emails under your domain without your consent or knowledge.
On top of this, they also ensure that the emails you send reach their desired recipient. Reducing the risk that they end up in a customer's or client’s spam folder or are flagged as a threat.
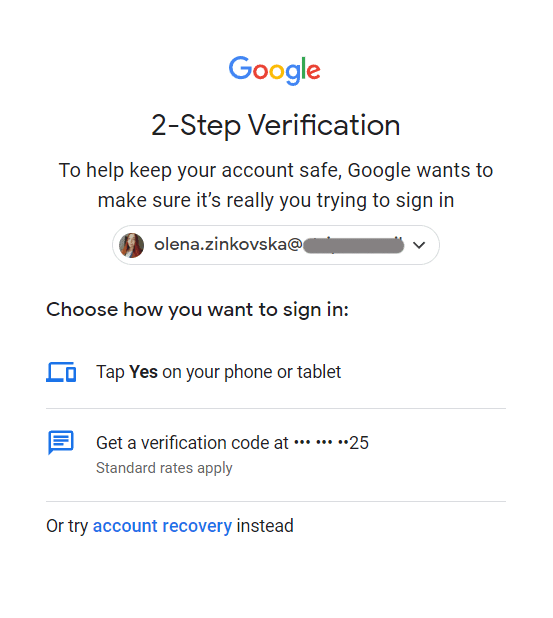
9. Enable two-factor authentication
Two-factor and multifactor authentication are great options that massively increase your email security.
This is how it works: when you log in to your email, you enter your password, which triggers a code sent to your smartphone for verification. Without this code, you can’t access your account, so even if a hacker were to get their hands on your password, your information would remain safe.
10. Update your OS
Regularly updating your operating system is vital for email security since updates can add new features. Updates also fix or patch any vulnerabilities in the system. Patches remove bugs and gaps that hackers could use to gain access to your computer and data.
11. Only trust reliable sources
If you receive an email with a link to click on, always check where that link is going to direct you before clicking on it. You can type the website address into your browser to ensure that it will not redirect you to a fake site.
If it looks suspicious for any reason, don't click on it, even if it appears to have been sent from someone you know. Instead, you should contact the person and ask if they sent you the email.
Learning the tell-tell signs of a phishing email can also save you a lot of stress and worry and is crucial in email management. The following are signs that an email is a scam, even if it looks like it comes from a company you trust and even uses its logo:
- a generic greeting or the first half of the email instead of your name. You know the drill: “Hello ant_man_fan78..”;
- the email claims that your account is on hold because of a billing problem;
- the email asks you to click on a link to update your payment details.
Real companies will never email or text with a link to update your payment information. It’s also extremely rare for legitimate companies to send emails with typos, which is another common sign of phishing emails. However, AI is making it easier for hackers to improve the grammar of phishing emails.
12. Enforce employee compliance
Finally, all of this information is useless unless applied, so ensure that your colleagues and employees (and employers!) are taking heed of email security protocols and applying them as necessary.
To stay ahead of the curve, make sure to regularly review and update your email lists and invest in reputable list management tools. Keeping up with the latest developments in email security can help protect your business from potential cyber-attacks. Review The Email List Decay Report for 2023 for more insights.
Wrapping up
Keeping your emails safe isn’t rocket science, but it requires some forethought and consideration, especially if you’re running a business of any size. No one is safe from hacking or looking like an attractive target.
This is why you need to protect your email and data and back everything up. Whether you’re an email marketer or an accountant at your company, if you work with emails (and almost all of us do), you need to know what’s up with security.





0 comments